Fast, but Exposed: The Silent Risk in CDN-Delivered Content
Performance has become a cornerstone of modern web development. Engineers are relentlessly optimizing systems to ensure users get blazing-fast experiences. One of our favorite tools in that pursuit? Content Delivery Networks (CDNs). We use CDNs to serve static assets like JavaScript, CSS, images, and HTML — and rightfully so. The benefits are real: global caching, reduced server load, better time-to-first-byte.
But in the race to ship fast, we often leave something critical behind: access control
The Problem: Security Stops at the Server
When we design secure systems, we think in terms of roles, permissions, authentication flows, rate limits, API gateways, OAuth tokens, and hardened servers. But we rarely ask: "What happens when private content gets served by a public CDN?"
This isn't a hypothetical risk. In 2010s, Facebook faced criticism for content lingering in its CDN long after users deleted it — profile pictures, albums, and more remained accessible via direct URLs. There was no authentication, no signed URLs, no expiration policies. Just a raw link serving supposedly private content.
The core issue? CDNs were treated like performance utilities, not part of the application’s trust boundary.
How We Got Here
CDNs were built to solve a performance problem. And from a pure networking standpoint, they do that beautifully. But in the modern web, not all static content is public:
A user’s private photo
A PDF receipt with personal data
Temporary access tokens embedded in HTML
Yet we often:
Host these on public URLs
Serve them without signed requests
Rely only on obscurity or randomness to protect them
Why This Is a System Design Problem
This isn't a coding bug. It's a flaw in architectural thinking — an incomplete threat model. We separate the backend (secured) from the frontend (static), forgetting that CDNs are simply edge storage. If we give them sensitive data without any policy enforcement, they’ll serve it to anyone who asks.
Symptoms of This Flaw
Deleted files still accessible via direct links
Logged-out users accessing sensitive images
URLs being guessable or leaked via referrers
No audit logs of who accessed what from CDN
What We Should Be Doing Instead
To protect users and data, we must elevate our expectations of CDNs. They should be part of our access control fabric.
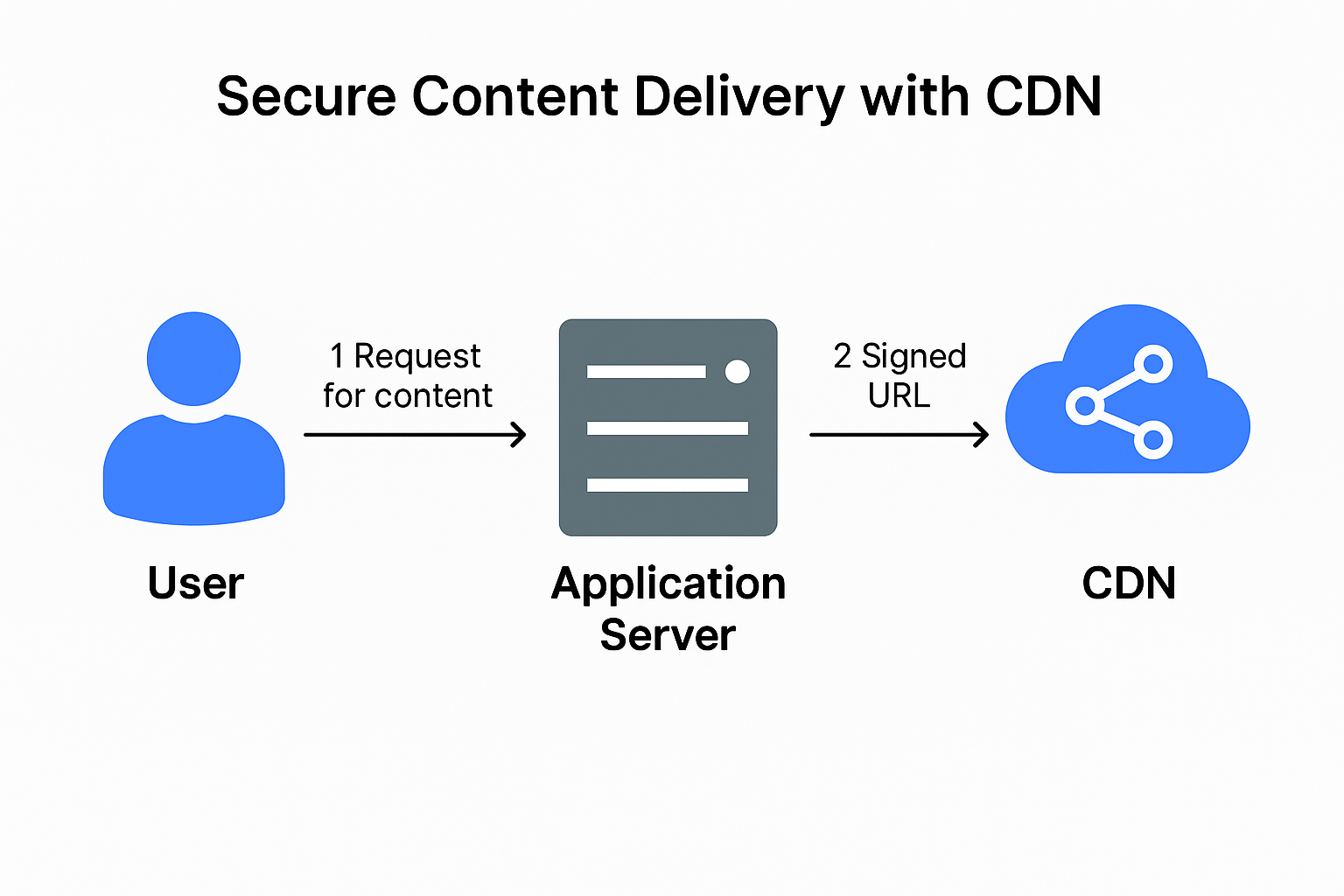
Use Signed URLs
Generate time-limited, user-bound access URLs for sensitive assets.
Enforce Expiry Policies
Set cache lifetimes that match the data’s lifecycle.Use Authenticated Edge Proxies
Serve content via edge functions (like AWS Lambda@Edge or Cloudflare Workers) that validate session/auth tokens before returning data.Incorporate CDN Layers into Your Threat Models
Your CDN knows more about your users than you think — treat it with the same scrutiny as your application server.Ensure Deletion Propagation
When users delete a file, purge it from the CDN in real time.
Conclusion
Performance and privacy are not mutually exclusive — but only if we bring both into every layer of our system design. CDNs should do more than cache and deliver. They should understand context, access, and intention.
As engineers, it's time we stop thinking of CDNs as just “dumb pipes.” They’re part of the application. And they deserve just as much security attention as our APIs and databases.
Remember: Fast is good. Fast and secure is better.