🔐 Encryption vs Hashing: A Tale of Two Secrets
From end-to-end encrypted WhatsApp messages to passwords for an account, there's a quiet battle happening under the hood — one that keeps your secrets, safe.
Let’s explore encryption and hashing — the two heroes of digital security — through real-world stories.
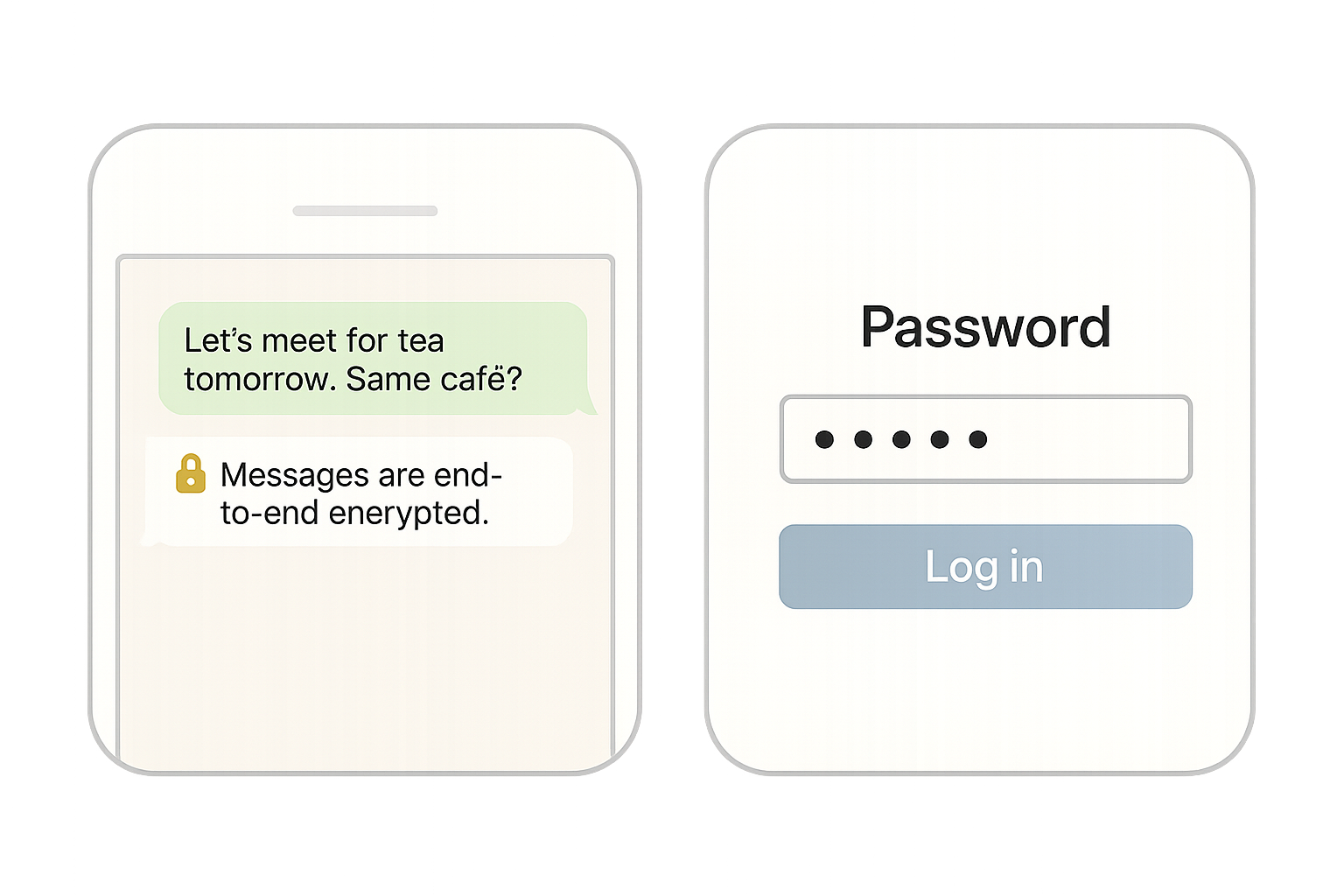
☕ Scene 1: "This Message Is End-to-End Encrypted"
You're sipping your chai and texting a friend on WhatsApp:
"Let’s meet for tea tomorrow. Same café?"
You hit send.
You see: “End-to-end encrypted.”
Cool. But what does that really mean?
🔐 Encryption: The Lock-and-Key
Think of encryption like putting your message in a sealed box that only your friend can unlock.
Before it leaves your phone: It’s scrambled using a secret key.
While it travels over the internet: It's unreadable to anyone, even the app provider.
At your friend's phone: It’s decrypted — turned back into plain text using their key.
Even WhatsApp can’t read it — that’s end-to-end encryption.
💡 Real-world use: Messaging apps, credit card transactions, file storage (Google Drive, Dropbox).
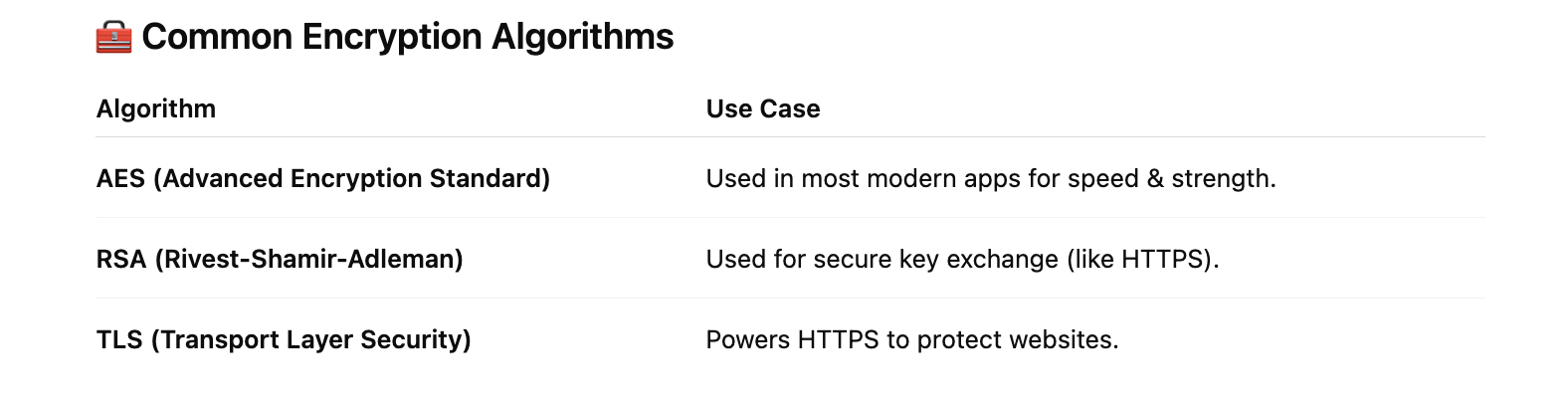
🧰 Common Encryption Algorithms
🔐 Scene 2: "Please Set Your Password"
Now you're signing up for a new app.
It asks you to create a password. You type: samosaLove@123
You wonder:
"Can someone at the company see my password?"
Thankfully, no. Not if they’re doing it right.
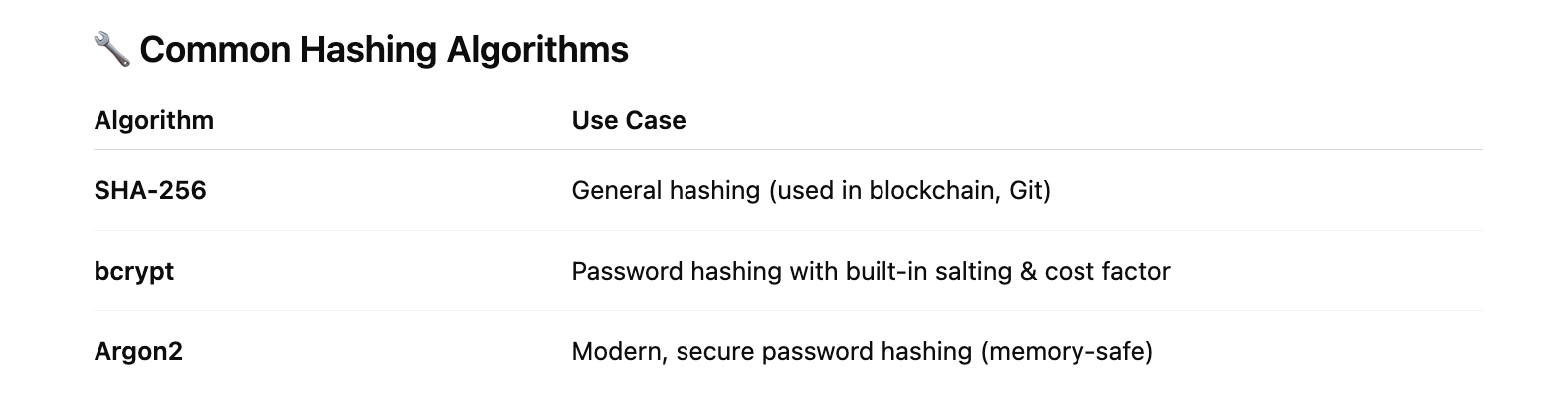
🔁 Hashing: The One-Way Blender
Hashing is like turning your password into a smoothie — you can see what came out, but you can’t get back the original fruits.
You type:
samosaLove@123The app runs it through a hash function (e.g., SHA-256)
It stores the result:
e99a18c428cb38d5f260853678922e03
Later, when you log in, your input is hashed again and compared.
No plain-text password is ever stored.
💡 Real-world use: Passwords, file verification, data fingerprinting.
🧂 What About Salting?
If everyone hashed password123, the result would always be the same. That’s dangerous.
To avoid this, systems add random data (a "salt") to the password before hashing:
password123 + randomSalt → hashed securely
Even if two users have the same password, their stored hashes look different.
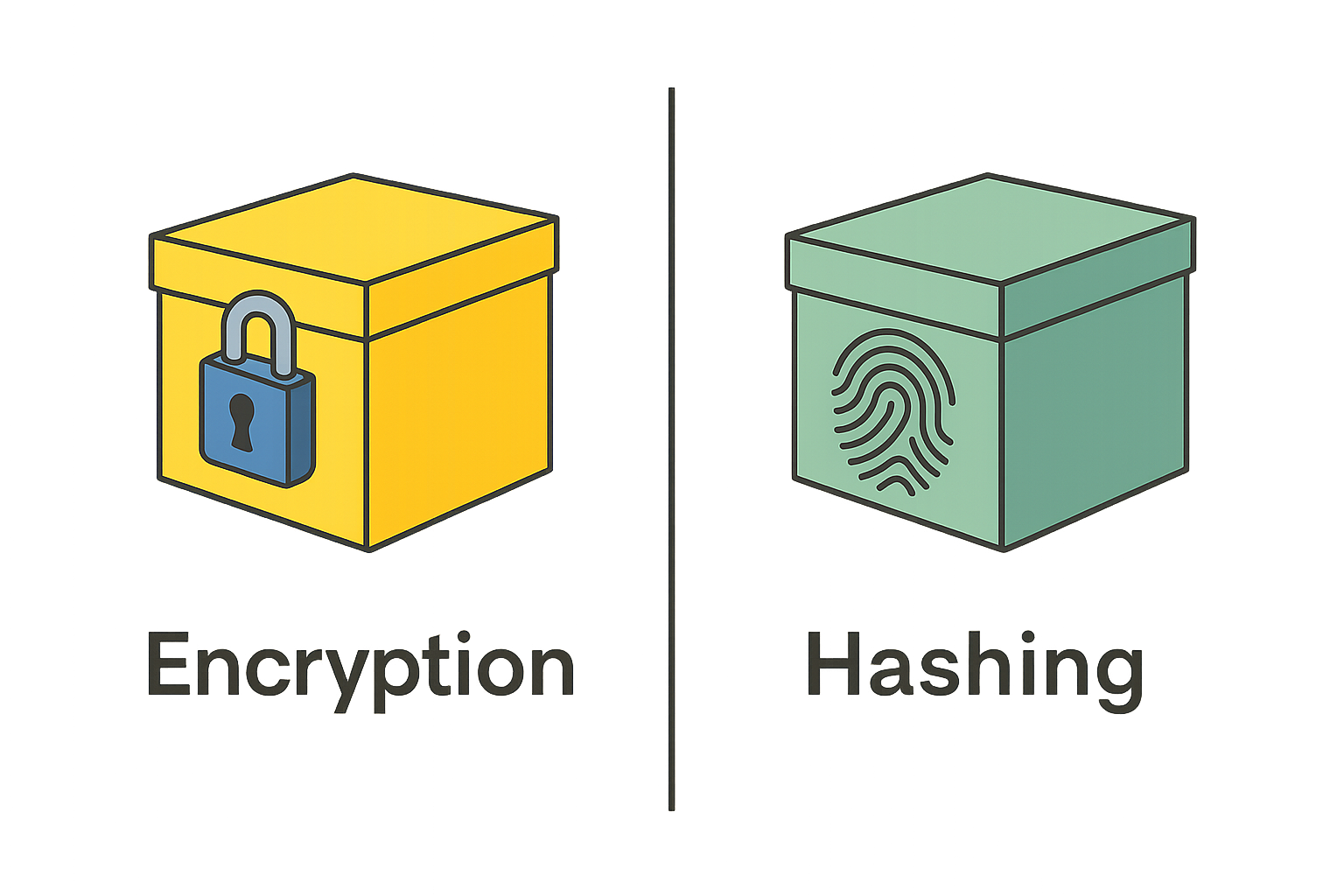
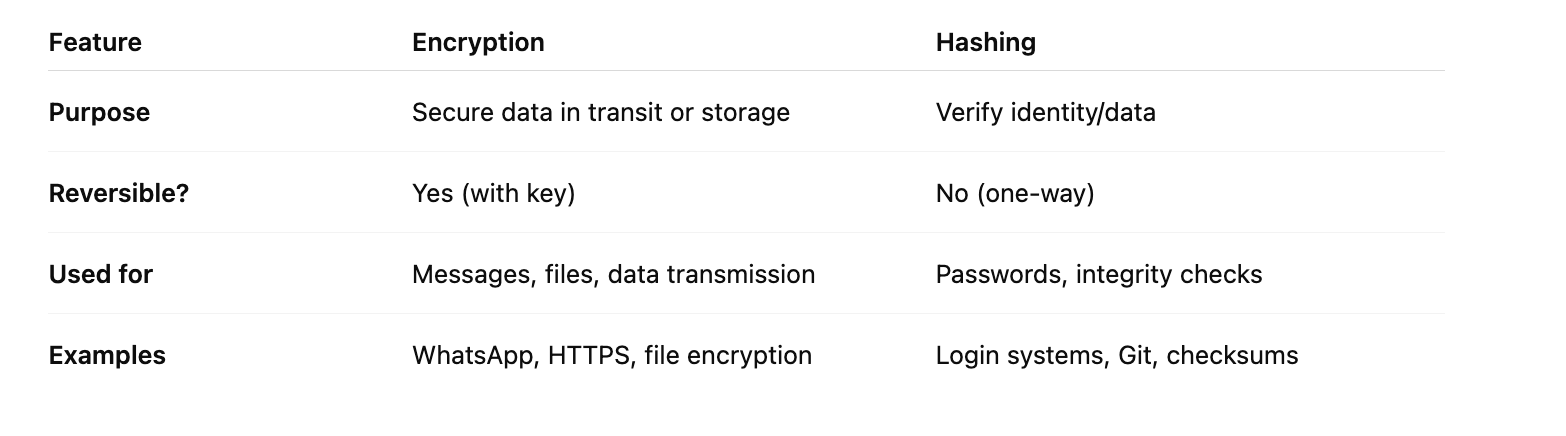
🤔 Encryption vs Hashing: A Quick Comparison
🧠 Why Should Engineers Care?
Whether you're building an app, designing a system, or just exploring, understanding how data is secured is no longer optional.
Knowing when to use encryption (privacy) and when to use hashing (integrity) is key to designing systems that protect users and scale securely.
📌 TL;DR: The Core Takeaway
Encryption keeps data private — useful when it needs to be read again.
Hashing keeps data verified — useful when it just needs to be matched.
🔍 Final Thought
So next time you:
See “end-to-end encryption” on your messages
Or wonder how an app remembers your password…
Know that somewhere, math is working behind the scenes. Quietly. Invisibly. Protecting your secrets.